The “Options” section allows you to configure various protection parameters:
Virtual Machine
- Version - this options allows to specify the version of virtual machine (the default value is the current version). Selecting "Compact" will use the old version of the virtual machine, which has a smaller bytecode size.
- Instances - this options allows to specify the number of the virtual machine copies (the default value is 10). Each virtual machine will have unique set of properties (different registers positions, different bytecode direction, different handlers of commands, etc.) that makes harder the analysis and hacking of virtualized code.
- Complexity - this options allows to specify the probability of creating complex handlers (consisting of several simple handlers) inside the virtual machine. This option also greatly complicates the analysis and hacking of virtualized code. As the complexity increases, the size of the protected file also increases.
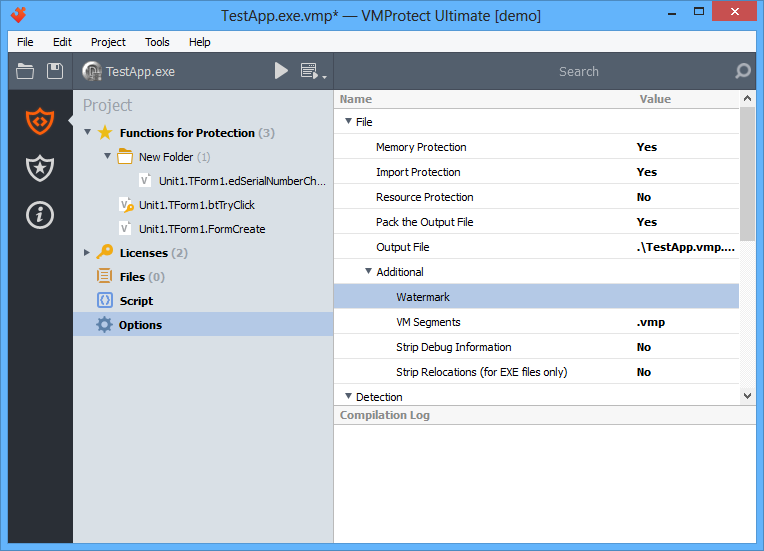
File
- Memory Protection – this option allows you to secure the image of the file in memory from any changes (data integrity is checked for all sections that do not have the WRITABLE attribute). Image integrity check is performed before passing the control to the original entry point of the program. If integrity is violated, a corresponding message is shown and the program stops execution.
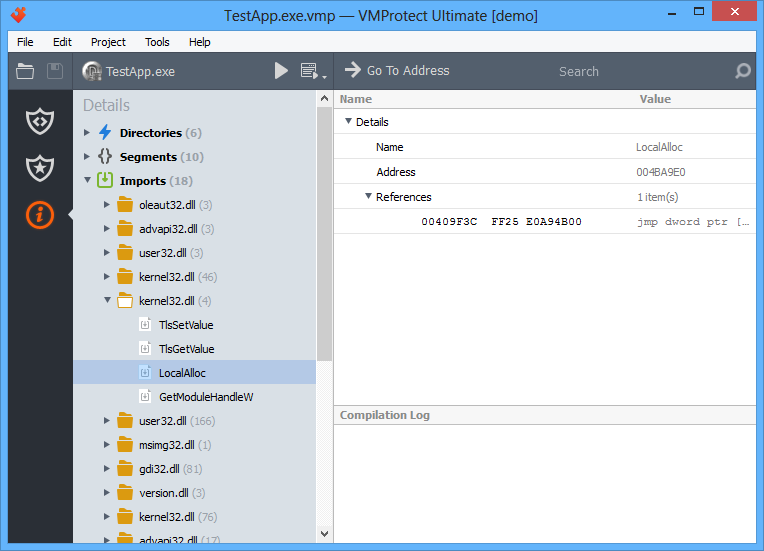
- Import Protection – this option allows hiding the list of API the protected program uses from a cracker. We recommend using this option along with packing of the output file.
- Resource Protection – this option encrypts resources of the program (except icons, manifests and other service resources).
- Pack the Output File – this option allows you to pack the protected file to reduce its size. The application is unpacked automatically when the protected file is executed. The entire unpacking goes without any disk writing, completely in RAM. When using this option, we also recommend to include EntryPoint to the list of protected objects.
!Important
When the program starts, after the code is unpacked the control is passed to EntryPoint. If the code of EntryPoint is virtualized, this code will be executed on the same VM interpreter as the code of the unpacker itself. Virtualization of EntryPoint combined with packing of the protected file prevents manual unpacking of the protected file, as in this case an intruder has to restore EntryPoint code to get a working file image.
Additional
- Segments – When the file is compiled, new segments will be added to it to the place where various system data are stored (virtualized and mutated code, VM interpreters, watermarks etc.). This option allows you to specify names for these new segments. We recommend changing the standard “.vmp” name of segments to something else (for example “.UPX”).
- Strip Debug Information – removing of debug information impedes analysis of the code by a cracker. For .NET applications this option also renames classes/methods/properties/fields except for those that were excluded from renaming.
- Strip Relocations – some compilers (i.e. Delphi) create a relocation table for EXE files that are not used by the operating system to load EXE files. If the option is enabled, the space occupied by relocation table is be used for VM needs.
- Watermark – allows adding watermark into the program.
- Lock To HWID – allows to lock the program to harware identifier.
Detection
- Debugger – this option prevents debugging of the protected file. There are 2 types of debuggers: User-mode debuggers (OllyDBG, WinDBG etc.) and Kernel-mode debuggers(SoftICE, Syser and others). Debugger detection is performed before passing control to the entry point of the program. If a debugger is detected, a corresponding message is shown and the program stops execution.
- Virtualization Tools – this option prohibits executing the protected file in various virtual environments: VMware, Virtual PC, VirtualBox, Sandboxie. Detection of virtualization is performed before passing control to the entry point of the program. If a virtual environment is detected, a corresponding message is shown and the program stops execution.
Messages
Here you can customize messages the program displays when it detects a debugger, a virtualization tool, if the file is corrupted or when there’s an attempt to execute the code protected by a serial number.
Licensing parameters
- File Name - choose a project file created in the license manager as a licensing parameter file. By default, the current project file is used.
- Activation Server - this option is required for activation system.